To make use of encapsulation, the encapsulating protocol must be open-ended, allowing for arbitrary data to placed in its messages. Another protocol can then be used to define the format of that data.
For example, consider an Internet host that requests a hypertext page over a dialup serial connection. The following scenario is likely:
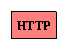
First, the HyperText Transfer Protocol (HTTP) is used to construct a message requesting the page. The message, the exact format of which is unimportant at this time, is represented as follows:

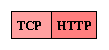
Next, the Transmission Control Protocol (TCP) is used to provide the connection management and reliable delivery that HTTP requires, but does not provide itself. TCP defines a message header format, which can be followed by arbitrary data. So, a TCP message is constructed by attaching a TCP header to the HTTP message, as follows:
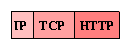
Now TCP does not provide any facilities for actually relaying a message from one machine to another in order to reach its destination. This feature is provided by the Internet Protocol (IP), which defines its own message header format. An IP message is constructed by attaching an IP header to the combined TCP/HTTP message:
Finally, although IP can direct messages between machines, it can not actually transmit the message from one machine to the next. This function is dependent on the actual communications hardware. In this example, we're using a dialup modem connection, so it's likely that the first step in transmitting the message will involve the Point-to-Point Protocol (PPP):
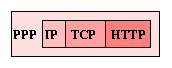
Note that I've drawn the PPP encapsulation a little differently, by enclosing the entire message, not just attaching a header. This is because PPP may modify the message if it includes bytes that can't be transmitted across the link. The receiving PPP reverses these changes, and the message emerges intact. The point to remember is that the encapsulating protocol can do anything it wants to the message - expand it, encrypt it, compress it - so long as the original message is extracted at the other end.